In the ever-evolving landscape of cybersecurity, traditional methods are proving insufficient against sophisticated threats. Enter Crowdstrike, a revolutionary cybersecurity solution that has been making waves in the industry. In this article, we will delve into the depths of Crowdstrike, understanding not only what it is but also how it works to safeguard digital environments.
I. Introduction
A. A Brief Overview of Crowdstrike
Crowdstrike is not just another cybersecurity company; it’s a game-changer. Established with the mission to reinvent cybersecurity, it has quickly become a leading force in the industry. Understanding the workings of Crowdstrike is crucial for businesses and individuals alike, as cyber threats continue to evolve at an alarming pace.
B. Importance of Understanding How Crowdstrike Works
With cyber threats becoming more sophisticated, having a basic antivirus program is no longer sufficient. Organizations need to adopt advanced solutions like Crowdstrike to stay ahead of the curve. This article aims to demystify the intricacies of Crowdstrike’s operations, providing a comprehensive guide for readers.
II. The Evolution of Cybersecurity
A. Traditional Cybersecurity Methods
Traditional cybersecurity relied heavily on signature-based detection and reactive measures. However, as cyber threats became more complex, these methods proved inadequate in preventing advanced attacks.
B. Need for Advanced Solutions
The escalating threat landscape necessitated the development of proactive and adaptive cybersecurity solutions. Crowdstrike emerged as a pioneer in this space, introducing a paradigm shift in how organizations approach cybersecurity.
III. Crowdstrike: An Overview
A. Company Background
Founded in [year], Crowdstrike has rapidly risen to prominence, serving as a beacon of innovation in the cybersecurity domain. The company’s commitment to continuous improvement and staying ahead of emerging threats has positioned it as a trusted partner for businesses globally.
B. Core Features and Services
Crowdstrike’s suite of services includes [list of services]. These core features are designed to provide comprehensive protection against a wide range of cyber threats.
IV. The Technology Behind Crowdstrike
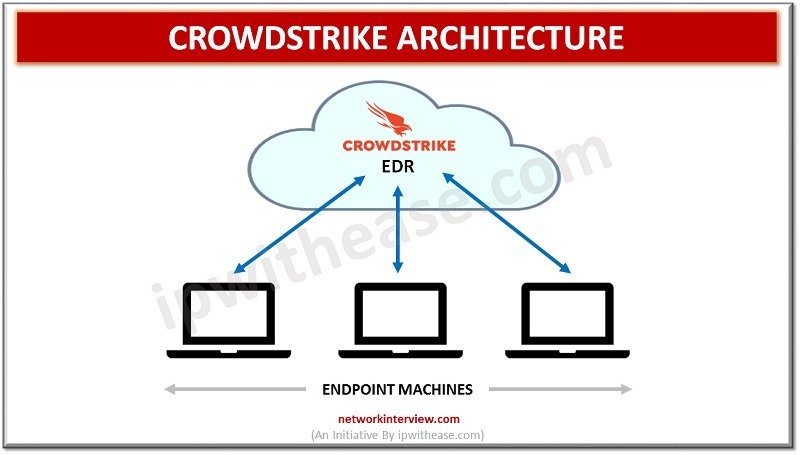
A. Endpoint Detection and Response (EDR)
At the heart of Crowdstrike’s technology is EDR, a proactive approach that focuses on identifying and responding to potential threats at the endpoint. This real-time monitoring ensures swift action against malicious activities.
B. Behavioral Analysis
Crowdstrike goes beyond traditional signature-based detection by employing behavioral analysis. This dynamic approach enables the system to recognize abnormal patterns and behaviors, even in the absence of known signatures.
C. Cloud-Native Architecture
Operating in the cloud allows Crowdstrike to deliver scalable and flexible security solutions. This cloud-native architecture ensures that the system can adapt to the evolving threat landscape seamlessly.
V. How Crowdstrike Works
A. Real-Time Threat Detection
Crowdstrike’s real-time threat detection capabilities are unparalleled. By continuously monitoring endpoints, it can identify and respond to potential threats the moment they occur, preventing widespread damage.
B. Incident Response and Mitigation
In the unfortunate event of a security incident, Crowdstrike’s rapid incident response capabilities come into play. The system facilitates quick and effective mitigation strategies, minimizing the impact on the organization.
C. Threat Intelligence
Crowdstrike leverages threat intelligence gathered from a vast network of sensors. This collective intelligence allows the system to stay ahead of emerging threats, providing users with proactive defense mechanisms.
VI. Key Advantages of Crowdstrike
A. Proactive Threat Hunting
Crowdstrike doesn’t wait for threats to materialize; it actively hunts for potential risks. This proactive approach sets it apart, ensuring that organizations are protected from both known and unknown threats.
B. Rapid Deployment and Scalability
Implementing Crowdstrike is seamless, with rapid deployment ensuring immediate protection. The system’s scalability further ensures that it can adapt to the growing needs of any organization.
C. Cloud-Based Security
The cloud-native architecture not only enhances flexibility but also enables organizations to embrace the benefits of cloud-based security. This is particularly crucial in the era of remote work and distributed computing.
VII. Case Studies
A. Successful Implementations
Numerous organizations across various industries have experienced the transformative power of Crowdstrike. Case studies highlight real-world scenarios where Crowdstrike’s intervention made a significant difference.
B. Impact on Cybersecurity Landscape
Crowdstrike’s presence has had a ripple effect on the cybersecurity landscape, influencing the way organizations approach and prioritize their security measures.
VIII. Challenges and Criticisms
A. Common Concerns
Despite its success, Crowdstrike is not immune to concerns and criticisms. Addressing these apprehensions head-on is crucial for fostering trust among potential users.
B. Addressing Misconceptions
Separating fact from fiction, this section aims to address common misconceptions surrounding Crowdstrike, providing a balanced perspective on its capabilities and limitations.
IX. Future of Crowdstrike
A. Emerging Trends in Cybersecurity
As the cybersecurity landscape continues to evolve, what does the future hold for Crowdstrike? This section explores emerging trends and how Crowdstrike plans to stay at the forefront of innovation.
B. Crowdstrike’s Role in the Evolving Landscape
With new challenges on the horizon, Crowdstrike’s adaptability and commitment to innovation position it as a key player in shaping the future of cybersecurity.
X. Conclusion
In conclusion, Crowdstrike is not just a cybersecurity solution; it’s a strategic investment in safeguarding digital assets. Understanding how Crowdstrike works is not merely a technical exercise but a proactive step toward fortifying defenses against the ever-present cyber threats.
FAQs
- Is Crowdstrike suitable for small businesses?
- Yes, Crowdstrike offers scalable solutions suitable for businesses of all sizes.
- How does Crowdstrike differ from traditional antivirus programs?
- Crowdstrike employs advanced techniques such as EDR and behavioral analysis, providing a more proactive and adaptive defense.
- Can Crowdstrike prevent all types of cyber threats?
- While highly effective, no security solution can guarantee 100% protection. Crowdstrike, however, significantly reduces the risk of successful cyber attacks.
- What industries benefit the most from Crowdstrike?
- Crowdstrike has proven beneficial across various industries, including finance, healthcare, and technology.
- Is Crowdstrike difficult to deploy and manage?
- No, Crowdstrike is designed for ease of deployment and management, ensuring a hassle-free experience for users.